Despite the importance of IoT security for enterprises, there is a lack of standards for the authentication and authorization of IoT devices. IoT SAFE, a new GSMA standard launched in 2021, aims to address this. Securing IoT application and data from ground, to cloud.
Click here to unlock more insights on the latest GSMA, cybersecurity and data privacy updates

A 2020 GSMA intelligence survey revealed that a whopping 98 percent of enterprises want an end-to-end connectivity solution. Similarly, a survey conducted by Beecham Research showed that seventy-one percent of enterprises consider security as a vital feature when selecting a solution.
Despite this emphasis on end-to-end security, there appears to be a lack of common standards for authentication of IoT devices. Piecemealing different facets of security from various solutions only increases IoT suite complexity. Leading to cost and time implications while hindering scalability and ease of management.
This is where IoT SAFE (IoT SIM Applet for Secure End-2-End Communication), a new GSMA standard, comes into play.
IoT SAFE at a Glance
IoT SAFE showcases that a SIM can be used as a Root of Trust (RoT). A highly reliable hardware, firmware, or software component that performs specific, critical security functions. Developed as a JavaCard application, IoT SAFE can be applied across various SIM form factors (e.g., SIMs, eSIMs, iSIMs).
With the SIM as a RoT, it assures device manufacturers, OEMs and service providers that all communications are secure. Guaranteeing the quality and integrity of all data.
IoT SAFE is also connectivity agnostic, meaning it works over various categories of cellular networks (e.g., 2G, 3G, 4G, 4G-LTE, 5G) and any IP connected device equipped with a SIM.
The approach also avoids duplication of secure hardware functions. By loading an additional security service for storing and processing the sensitive credentials used to establish the TLS handshake.
How does it work?
Transport Layer Security (TLS), or Datagram Transport Layer Security (DTLS2) are widely adopted security protocols. Designed to facilitate privacy and data security with authenticated encryption for communications, end-to-end. These also help protect against data breaches and other attacks.
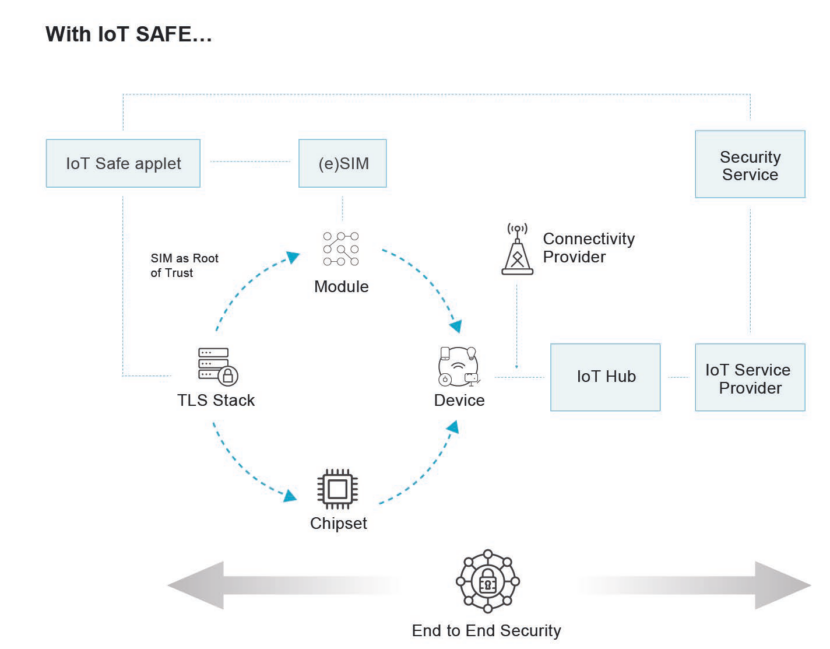
IoT SAFE is embodied as a JavaCard Applet that resides inside the SIM and comes in 2 variants.
- Type I – uses digital certificates for authentication of server and devices;
- Type II – uses pre-shared keys for authentication for more constrained devices
Either variant allows the SIM to perform all the security critical operations during the TLS or DTLS2 establishment phase. They provide a set of standard interfaces to manage the TLS handshake, leading to the generation of session keys.
The SIM securely stores credentials for these protocols. TLS stack providers can utilize IoT SAFE credentials and cryptographic services the same way.
These attributes essentially allow the SIM to perform a dual role:
- Application-layer security; and
- Mobile network authentication
IoT SAFE carries out mutual authentication of the IoT device and a remote server, establishing the session keys used for the data exchange.
Key Features & Benefits of IoT SAFE
- IoT Devices can securely perform mutual TLS/DTLS2 authentication to a server using either asymmetric or symmetric security schemes
- IoT devices to compute shared secrets and keep long-term keys secret
- Zero touch provisioning (ZTP) and credential lifecycle management from a remote IoT security service
This simplifies deployments as it does not require specific network functions or many-to-many integration scenarios. For example, between clouds, servers, IoT service providers and/or mobile network operators.
IoT SAFE also manages the complexity of setting up and on-going lifecycle of security credentials. The IoT Device Applications do not need to worry about any of the TLS security handshakes happening “under-the-hood”. Developers are then free to focus on their IoT applications.
ZTP automates the process of updating operating systems, installing patches and bug fixes. It essentially removes the need for IT personnel to manually configure devices, instantly reducing the risk of human error and allowing IoT connectivity to scale effortlessly. For a large IoT deployment with thousands of devices to provision and configure, the time and effort savings are significant.
IoT Trust, a Step Beyond IoT SAFE
While IoT SAFE is a fantastic initiative, its limitations are that it utilizes only specific hyperscaler clouds. For example, GCP, AWS or Azure. At ZARIOT, we’ve made IoT security more accessible through our partnership with atsign with our award winning joint solution – IoT Trust.

With IoT Trust, data remains fully end-to-end encrypted with uncompromisable data integrity. Data sharing is also fully controlled by the data owner, meaning it can only be viewed and used with authorisation.
IoT Trust further saves on hardware investments as it can be retrofitted to any IoT device equipped with an eUICC SIM. It also reduces administrative costs by eliminating the need to administer IPs and VPNs.
Overall, this simplifies secure access to devices for configuration and maintenance, allowing you to deploy projects faster while lowering operational and management costs. IoT Trust also facilitates regulatory compliance such as GDPR and industry specific criteria like HIPPA.
To learn more about IoT Trust and additional features in our connectivity suite, or contact one of our industry experts today. Otherwise, feel free to read more about our award-winning solutions here and here.












Leave a Reply