By 2025, 5 billion IoT devices will achieve connectivity over cellular networks. Do you know how many protocols and layers are used to transmit data on a cellular network? Hackers do. And they know all the vulnerabilities and access points too. You’ve probably read more than a few headlines about mobile phones being hacked through the network itself. In fact, one can simply Google “how to hack a phone over signalling protocols”. You will also find that a single network may face thousands of attacks per day.
Many IoT and M2M devices work in critical systems such as surveillance, medical, and transport. Risks are sharply in focus when we think of pacemakers or surveillance cameras. For a water meter, on the other hand, security might seem of lesser concern, but consider 10,000 water meters in one city. The level of security required for a device depends on the device itself, location, final application and quantity of devices, however all devices are vulnerable to the same kinds of attacks over mobile network infrastructure.
Here we will focus on one of the lesser known, yet arguably most important aspects of securing an IoT device: the protection of the device identity, or IMSI, which is the critical information contained in the SIM card itself. This identity is a key component in mobile network authentication management and data transmission over mobile networks. You may think devices with IP and application layer security features are protected, but that’s only half the story.
Signalling and IoT Devices
IoT devices like remote sensors, meters and smart vehicles obtain their connectivity through a cellular connection. In every one of these is a SIM card of some shape or form that provides the user identity and authenticates the device on the telecom’s network infrastructure. Short-range devices such as smart plugs and most smart watches connect to the internet through WiFi or bluetooth with no need for cellular.
“Signalling” is the process that devices and network elements use to authenticate, manage and control the devices, SIMs, and their data through the mobile network. It is in this complex realm of large mobile network operators (MNOs) that security often comes as an afterthought. Here, the user’s private data may not be as secure as once thought. ZARIOT hopes to shed light on this issue and make enterprises aware of the dangers of being connected, and the importance of being protected.
What is SS7?

Let’s start by looking back to a time when the world was a simpler place: the 1970s. Concorde was soaring high, the Rolling Stones were re-inventing rock and Signalling System 7 (SS7) was created.
SS7 is a telephone protocol used to set up and switch off connections on a cellular network. It formed the backbone of the telecoms infrastructure in the form of voice, SMS and data from the 1970s up until the emergence of LTE networks 40 years later for 4G onwards which use a newer protocol called Diameter.
Even though the world seems to be switching to 4G (and 5G), 2G and 3G are still widely used, and SS7 is therefore still the most common protocol in use for telecoms communication today. In fact, SS7 continues to survive even in Diameter 4G networks as it is required for both voice calls and sending SMS.
At the time SS7 was created, most (if not all) MNOs trusted each other and, because of this trust, openly shared communication with each other. It was a situation where there was safety in isolating infrastructure in this close-knit family of operators. Life was good and everyone was happy.
SS7 Was Never Secure

This trust between networks led to security being taken for granted in the design of the protocol. As virtual operators (MVNOs) became commonplace, there was a substantial increase in the number of network carriers operating in the industry. More carriers meant more connections being made by technicians with limited core knowledge and skill in the telecoms area. The limited pool of skilled SS7 engineers led to vulnerabilities in the SS7 network in the form of unsecured grey routes, misconfigured network nodes and untrusted parties gaining access to network infrastructure.
The mobile landscape has changed a lot since the inception of SS7. The world is no longer limited to the single, wired phone hooked up in the hallway. The increased number of mobile devices has naturally resulted in a dramatic increase in signalling traffic. Additionally, networks are now expected to accommodate calls, SMS, and data, which is far more than the original design was intended for.
As the use cases for the network have changed drastically, attackers have identified security holes in networks that could not have been foreseen when SS7 was designed. Security that hinged on the legitimacy of the small number of interconnected networks themselves is long outdated.
Aren’t new mobile networks secure? No.

One of the best things about the way in which mobile generations work is that they build on top of the base protocol SS7. This meant that MNOs could prepare for each new generation in a familiar way and provide better services at a faster pace. SS7 is still part of 1G, 2G and 3G networks. 4G LTE devices that operate on the newer protocol called Diameter even use SS7 as a fallback in case they cannot get 4G service.
Unfortunately, in terms of security, this is also the worst thing. Like building a house on a weak foundation, using SS7 as a building block for multiple generations meant that all of the weaknesses that were present in the initial version continued to be exploited as the technology advanced. Diameter, the newer network protocol that 4G LTE networks are based on, was designed with more security in mind, however it inherited all weaknesses from SS7 and additionally has more access and entry points for attacks than SS7.
This is where IoT devices suffer greatly
In many cases, IoT devices consume low volumes of data and SMS. This is especially true for telematics devices such as meters and sensors which often only transmit a few bytes per hour. A quick benefit analysis may lead enterprises to use older, cheaper and more widely available technologies like 2G and 3G for their devices. Since these generations have existed for the longest amount of time, they are actually the most insecure, as their weaknesses are well documented and widely available.
Purpose-built radio technology such as LoRa appeared to suit the business case for cheap, low data transmission, but adoption has been slow and coverage is often not available. Although encryption is used for security, it is plagued with its own litany of vulnerabilities.
While there are ongoing efforts by MNOs to deploy 5G, it will still be a few years until the rollout is complete, meaning IoT manufacturers are left in a limbo of which mobile generation to choose from, but make no mistake — all of them have inherent security concerns — especially 5G.
Let’s dive into some of the specifics about mobile network vulnerabilities. Various network components may be integral to an attack, however the HLR is the most notable.
What is HLR/HSS?

A home location register (HLR) is the subscriber database that stores the details of all permanent subscribers of an SS7 network. A home subscriber server (HSS) is the same component, but in a Diameter network. Each subscriber is represented by an individual mobile subscriber identity, or IMSI. This is a unique number used for contacting the SIM card. The HLR or HSS represents the single source of truth for IMSI information such as its location, how to contact it and the services it is allowed to access.
What vulnerabilities does an HLR/HSS have?
Being a source of trust, data in the HLR and HSS is very sensitive. If an attacker can access an HLR or HSS, it can get access to information about a subscriber, that can be used to carry out a variety of attacks.
From the mobile phone number subscriber directory (MSISDN) housed in the HLR/HSS, hackers can retrieve IMSI and visitor location registration (VLR) or support node (SGSN) location. The SGSN is the component in mobile networks that allows the transmission of IP packets to the internet or other external networks.
With IMSI and VLR/SGSN location, users can perform attacks on the device itself. Also, hackers can send messages to the HLR or HSS modifying customer settings that could alter the customer profile and the service.
For example:
- One could send a fake location message to the HLR to intercept SMS or get the device disconnected due to misbehaviour.
- If you wanted to track the location of a device, you could repeatedly ping the HLR.
- A denial of service (DoS) attack can be performed by sending a message to the HLR to disable all services.
- Should an attacker have physical access to a device, they could steal and fraudulently repurpose the SIM card, then access the HLR to enable voice services and make phone calls on your account.
- If one were so determined, they could even access the data transmitted to and from the device by accessing the HLR.
Without signalling security, these attacks are possible despite other security measures taken to protect data over the IP layer like encryption and secure software.
IoT Attacks Over Signalling Protocols

IoT attacks can be separated into three categories: privacy, fraud and denial of service. All of these attacks can be committed once an attacker has gained access to the network, regardless of the device security or IP layer security.
- Privacy can be compromised when a hacker sends a message to a network node, such as a visitor location register (VLR), that can essentially ask for subscriber information. Sensitive information such as location and contact details can be exposed. This is also called device tracking.
- Fraud includes many tactics, but most involve stealing information to gain access to private accounts or services. An example of this would be redirection of SMS, or SMS interception. An attacker could send a message to the network (VLR) telling it to overwrite a subscriber’s details with their own. In this way, hackers change the number the password would be sent to so that they receive the SMS messages themselves. Data can also be intercepted by updating the packet data protocol. Data interception is also a privacy breach, and as is the case with most attacks, one breach then leads to another.
- Denial of service attacks involve disabling a device from connecting or getting service from the network. This can be done a number of ways ranging from simply unregistering the device from the network (cancel location message) to updating its network profile (insert subscriber data), effectively disconnecting the device. These messages may disable the sending or receiving of SMS or data for variable lengths of time.
Security Solutions
ZARIOT offers a three-pronged approach to tackling security issues:
- Best in Class Signalling firewall
- VPN – Secure virtual private network connection
- APN lock
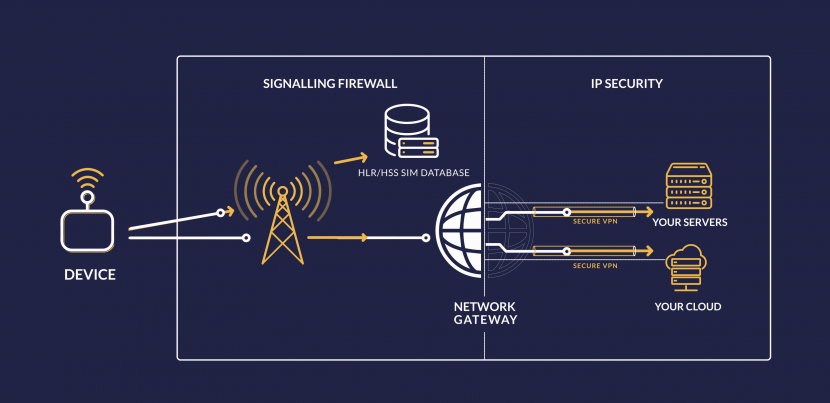
When combined, these approaches result in end-to-end security from the device to an enterprise’s private servers or cloud. Signalling security protects devices from attack and data as it travels through the mobile network. From the ZARIOT platform, we can send data securely to private data centers through a secure VPN. The APN lock ensures device authenticity and provides endpoint security.
Signalling Firewall
ZARIOT leverages the power of the award-winning Cellusys Unified Signalling Firewall to secure our core network infrastructure including SS7, Diameter, SMS, GTP, and SIP protocols. With industry leaders able to control and update the firewall on our network, we are in the best position to offer the world’s first global IoT SIM with signalling security.
The Unified Signalling Firewall works by filtering out malicious messages from the network using a comprehensive rule engine that is able to identify incorrect or dangerous parameters and take action. Using internal correlation and cross-protocol analysis, complex threat scenarios are easily recognized and mitigated. The firewall provides full compliance with GSMA security standards FS.11, FS.19, FS.21 and IR.70.
With over 15 years of expertise in signalling security, the ZARIOT Unified Signalling Firewall is expertly monitored, adjusted, and updated in the face of emerging threats and industry recommendations ensuring the highest level of signalling security available is always maintained.
A signalling firewall is the only way to protect the cellular connectivity of IoT devices.
VPN Connection
A VPN secures the internet protocol (IP) layer connection on your device’s communication. This means that its data is fully encapsulated in an encrypted payload with strong, modern cyphers that are generated on a per-customer basis.
A hashing mechanism can then verify whether a message was tampered with while in transit. Identified tampering might indicate a potential man-in-the-middle attack or data interception.
VPN connections can be extended to guarantee end-to-end encryption from the ZARIOT core platform to your network operation center or private data center.
APN Lock
An APN is a gateway that enables a device to connect to the data network. The ZARIOT APN Lock delivers a username and password combination that is unique to a device.
When enabled, the APN Lock requires each device to authenticate with this username and password if it is to be granted connectivity. This provides endpoint security as the SIM card is secured against being “re-purposed” by an attacker. Protection from these attacks may save thousands in usage and overage fees, and prevent your device from being recruited into a botnet.
To achieve end-to-end security, devices with SIM cards must be protected against both IP layer (internet-based) attacks as well as signalling-based attacks.
ZARIOT is the only connectivity solution that provides the global coverage of cellular connectivity, with the security over signalling protocols that cellular demands to protect devices and data. Test our SIMs in your devices with no obligation, or contact us for more information on signalling security and how we can help connect and protect your IoT project.












Leave a Reply